Hello, I have a .net7 minimal api running over Kestrel in VS Code. I have negotiate authentication setup for windows auth and it works correctly when hitting any endpoints in the browser or when the app is deployed to IIS.
The problem is that when we try to use postman to hit the endpoints locally we always receive a 401 even with NTLM auth setup with the correct credentials. It doesnt even seem like it hits our middleware. I have SSL disabled in postman and no certificates set.
"https": {
"commandName": "Project",
"dotnetRunMessages": true,
"launchBrowser": false,
"applicationUrl": "https://localhost:7297;http://localhost:5209",
"environmentVariables": {
"ASPNETCORE_ENVIRONMENT": "Development"
},
"windowsAuthentication": true,
"anonymousAuthentication": false
},
builder.Services.AddAuthentication(NegotiateDefaults.AuthenticationScheme)
.AddNegotiate();
builder.Services.AddAuthorization(options =>
{
options.FallbackPolicy = options.DefaultPolicy;
});
app.UseAuthentication();
app.UseAuthorization();
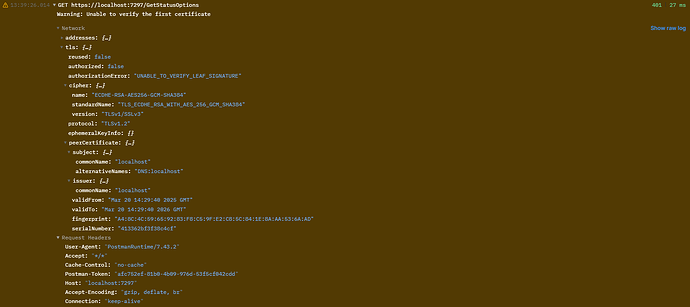
Here is the console log in postman:
GET https://localhost:7297/GetStatusOptions4015 ms
Warning: Unable to verify the first certificate
 Network
Network
-
 addresses: {…}
addresses: {…} -
 local: {…}
local: {…}
1. address: "::1"
2. family: "IPv6"
3. port: 63028
 remote: {…}
remote: {…}
1. address: "::1"
2. family: "IPv6"
3. port: 7297
-
 tls: {…}
tls: {…} -
reused: false
-
authorized: false
-
authorizationError: “UNABLE_TO_VERIFY_LEAF_SIGNATURE”
-
 cipher: {…}
cipher: {…}
1. name: "ECDHE-RSA-AES256-GCM-SHA384"
2. standardName: "TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384"
3. version: "TLSv1/SSLv3"
-
protocol: “TLSv1.2”
-
ephemeralKeyInfo: {}
-
 peerCertificate: {…}
peerCertificate: {…}
1. ▶subject: {…}
1. commonName: "localhost"
2. alternativeNames: "DNS:localhost"
2. ▶issuer: {…}
1. commonName: "localhost"
3. validFrom: "Dec 4 17:08:56 2024 GMT"
4. validTo: "Dec 4 17:08:56 2025 GMT"
5. fingerprint: "D2:E6:51:B1:70:A5:8C:CD:B8:E4:0A:60:CB:42:BD:CD:F6:99:C0:6C"
6. serialNumber: "8e8de005f9957524"
![]() Request Headers
Request Headers
User-Agent: PostmanRuntime/7.43.2
Accept: /
Cache-Control: no-cache
Postman-Token: 9ba8828a-84c7-40a1-940c-327102498669
Host: localhost:7297
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
![]() Response Headers
Response Headers
Content-Length: 0
Date: Wed, 19 Mar 2025 14:37:24 GMT
Server: Kestrel
WWW-Authenticate: Negotiate
![]() Response Body
Response Body